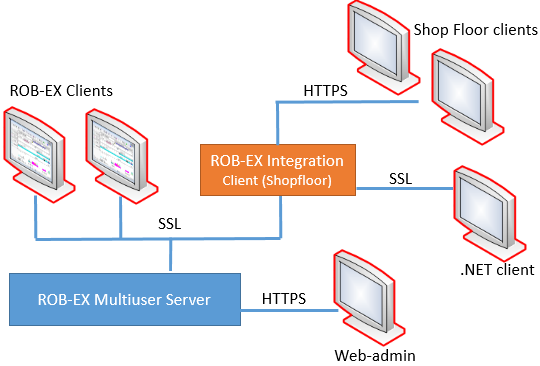
This section describes how to enable secure networking communication between the different components of the ROB-EX system. Enabling SSL means that traffic between server and cliens are encrypted and that web-server sessions with the Multiuser admin web pages web pages must be accessed through https in the browser.
This manual is divided into the following sections, explaining how to enable secure communication for the different components
Multiuser Server
SSL communication with the Multiuser is by default turned off. To enable this feature one has to change the configuration by hand editing different files of the Multiuser installation. Start out by locating the location on the file system where your server is installed. If in doubt locate the Server service (Run->Services.msc and locate the ROB-EX Multiuser Service for instance X). Double click on the service and take a note of the “Path to executable:”.
Since the client and server are using different types of communication, configuration needs to be done in 4 different areas.
- Client->Server communication
- Event based communication
- Services
- Web based communication
- Step 8 – edit
deploy\jbossweb-tomcat50.sar\server.xml
- Step 8 – edit
Client->Server communication
This section describes the changes needed to communicate securely between the ROB-EX clients and the Server Service.
Step 1
At first copy SSL keystore and truststore files from ganttServer\server\gantt\ssl\conf folder into the ganttServer\server\gantt\conf folder. More information about how to install own certificate files can be found in the chapter Keystore and truststore.
Step 2
Add the following part to the ganttServer\server\gantt\conf\standardjboss.xml file. Must be inserted at the top of the file just below the first <invoker-proxy-bindings> tag:
<!-- ===================================================================== -->
<!-- SSL START insert after first <invoker-proxy-bindings> tag -->
<!-- ===================================================================== -->
<invoker-proxy-binding>
<name>stateless-ssl-rmi-invoker</name>
<invoker-mbean>jboss:service=invoker,type=jrmp,socketType=SSL</invoker-mbean>
<proxy-factory>org.jboss.proxy.ejb.ProxyFactory</proxy-factory>
<proxy-factory-config>
<client-interceptors>
<home>
<interceptor>org.jboss.proxy.ejb.HomeInterceptor</interceptor>
<interceptor>org.jboss.proxy.SecurityInterceptor</interceptor>
<interceptor>org.jboss.proxy.TransactionInterceptor</interceptor>
<interceptor call-by-value="false">org.jboss.invocation.InvokerInterceptor</interceptor>
<interceptor call-by-value="true">org.jboss.invocation.MarshallingInvokerInterceptor
</interceptor>
</home>
<bean>
<interceptor>org.jboss.proxy.ejb.StatelessSessionInterceptor</interceptor>
<interceptor>org.jboss.proxy.SecurityInterceptor</interceptor>
<interceptor>org.jboss.proxy.TransactionInterceptor</interceptor>
<interceptor call-by-value="false">org.jboss.invocation.InvokerInterceptor</interceptor>
<interceptor call-by-value="true">org.jboss.invocation.MarshallingInvokerInterceptor
</interceptor>
</bean>
</client-interceptors>
</proxy-factory-config>
</invoker-proxy-binding>
<invoker-proxy-binding>
<name>stateful-ssl-rmi-invoker</name>
<invoker-mbean>jboss:service=invoker,type=jrmp,socketType=SSL</invoker-mbean>
<proxy-factory>org.jboss.proxy.ejb.ProxyFactory</proxy-factory>
<proxy-factory-config>
<client-interceptors>
<home>
<interceptor>org.jboss.proxy.ejb.HomeInterceptor</interceptor>
<interceptor>org.jboss.proxy.SecurityInterceptor</interceptor>
<interceptor>org.jboss.proxy.TransactionInterceptor</interceptor>
<interceptor call-by-value="false">org.jboss.invocation.InvokerInterceptor</interceptor>
<interceptor call-by-value="true">org.jboss.invocation.MarshallingInvokerInterceptor</interceptor>
</home>
<bean>
<interceptor>org.jboss.proxy.ejb.StatefulSessionInterceptor</interceptor>
<interceptor>org.jboss.proxy.SecurityInterceptor</interceptor>
<interceptor>org.jboss.proxy.TransactionInterceptor</interceptor>
<interceptor call-by-value="false">org.jboss.invocation.InvokerInterceptor</interceptor>
<interceptor call-by-value="true">org.jboss.invocation.MarshallingInvokerInterceptor</interceptor>
</bean>
</client-interceptors>
</proxy-factory-config>
</invoker-proxy-binding>
<!-- ===================================================================== -->
<!-- SSL END -->
<!-- ===================================================================== -->Find (part of <container-configuration> tag for stateless sessions beans)
<invoker-proxy-binding-name>stateless-rmi-invoker</invoker-proxy-binding-name>and change it to:
<invoker-proxy-binding-name>stateless-ssl-rmi-invoker</invoker-proxy-binding-name>Next find the (part of <container-configuration> tag for stateful sessions beans)
<invoker-proxy-binding-name>stateful-rmi-invoker</invoker-proxy-binding-name>and change it to:
<invoker-proxy-binding-name>stateful-ssl-rmi-invoker</invoker-proxy-binding-name>Step 3
Open file ganttServer\server\gantt\conf*jboss-service.xml in editor. Search for this part below
<!-- RMI/JRMP invoker -->
<mbean code="org.jboss.invocation.jrmp.server.JRMPInvoker"
name="jboss:service=invoker,type=jrmp">
<attribute name="RMIObjectPort">4444</attribute>
<attribute name="ServerAddress">${jboss.bind.address}</attribute>
<!--
<attribute name="RMIClientSocketFactory">custom</attribute>
<attribute name="RMIServerSocketFactory">custom</attribute>
<attribute name="SecurityDomain">ssl-domain-name</attribute>
-->
<depends>jboss:service=TransactionManager</depends>
</mbean>Insert the following after the above:
<!-- The SSL domain setup -->
<mbean code="org.jboss.security.plugins.JaasSecurityDomain"
name="jboss.security:service=JaasSecurityDomain,domain=RMI+SSL">
<constructor>
<arg type="java.lang.String" value="RMI+SSL"/>
</constructor>
<attribute name="KeyStoreURL">resource:.keystore</attribute>
<attribute name="KeyStorePass">XXXXXXXXXXXX</attribute>
</mbean>
<mbean code="org.jboss.invocation.jrmp.server.JRMPInvoker"
name="jboss:service=invoker,type=jrmp,socketType=SSL">
<attribute name="RMIObjectPort">14445</attribute>
<attribute name="ServerAddress">${jboss.bind.address}</attribute>
<attribute name="RMIClientSocketFactory">
org.jboss.security.ssl.RMISSLClientSocketFactory
</attribute>
<attribute name="RMIServerSocketFactory">
org.jboss.security.ssl.RMISSLServerSocketFactory
</attribute>
<attribute name="SecurityDomain">java:/jaas/RMI+SSL</attribute>
<depends>jboss:service=TransactionManager</depends>
<depends>jboss.security:service=JaasSecurityDomain,domain=RMI+SSL</depends>
</mbean>Note, the password has been left out of this manual on purpose due to security reasons. Lookup the actual password from the file ganttServer\server\gantt\ssl\conf\jboss-service.xml
Event based communication (JMS)
This section describes the changes needed to secure the event based communication between going from server to the clients.
Step 4
Remove (it is not enough to rename!) the ganttServer\server\gantt\deploy\jms\uil2-service.xml file and create the following two files:
ganttServer\server\gantt\deploy\jms\ssl-domain-service.xml
<?xml version="1.0" encoding="UTF-8"?>
<server>
<mbean code="org.jboss.security.plugins.JaasSecurityDomain"
name="jboss.security:service=JaasSecurityDomain,domain=SSL">
<constructor>
<arg type="java.lang.String" value="SSL"></arg>
</constructor>
<attribute name="KeyStoreURL">resource:.keystore</attribute>
<attribute name="KeyStorePass">XXXXXXXXXXXX</attribute>
</mbean>
</server>Note, the password has been left out of this manual on purpose due to security reasons. Lookup the actual password from the file ganttServer\server\gantt\ssl\deploy\jms\ssl-domain-service.xml
Step 5
ganttServer\server\gantt\deploy\jms\ssl-uil2-service.xml
<?xml version="1.0" encoding="UTF-8"?>
<server>
<mbean code="org.jboss.mq.il.uil2.UILServerILService"
name="jboss.mq:service=InvocationLayer,type=SSLUIL2">
<depends optional-attribute-name="Invoker">jboss.mq:service=Invoker</depends>
<!-- JNDI binding -->
<attribute name="ConnectionFactoryJNDIRef">ConnectionFactory</attribute>
<!-- JNDI binding for XA -->
<attribute name="XAConnectionFactoryJNDIRef">XAConnectionFactory</attribute>
<!-- The bind address -->
<attribute name="BindAddress">${jboss.bind.address}</attribute>
<attribute name="ServerBindPort">8193</attribute>
<attribute name="PingPeriod">60000</attribute>
<attribute name="EnableTcpNoDelay">true</attribute>
<!-- Used to disconnect the client if there is no activity -->
<!-- Ensure this is greater than the ping period -->
<attribute name="ReadTimeout">120000</attribute>
<!-- Ensure this is greater than the ping period -->
<attribute name="ClientReadTimeout">120000</attribute>
<!-- The size of the buffer (in bytes) wrapping the socket -->
<!-- The buffer is flushed after each request -->
<attribute name="BufferSize">2048</attribute>
<!-- Large messages may block the ping/pong -->
<!-- A pong is simulated after each chunk (in bytes) for both reading and writing -->
<!-- It must be larger than the buffer size -->
<attribute name="ChunkSize">1000000</attribute>
<attribute name="ClientSocketFactory">org.jboss.security.ssl.ClientSocketFactory</attribute>
<attribute name="ServerSocketFactory">org.jboss.security.ssl.DomainServerSocketFactory</attribute>
<attribute name="SecurityDomain">java:/jaas/SSL</attribute>
</mbean>
<!--
Two JNDI bindings that act like jms client connections remotely
but have j2ee defined semantics inside JBoss
-->
<mbean code="org.jboss.naming.LinkRefPairService"
name="jboss.jms:alias=QueueConnectionFactory">
<attribute name="JndiName">QueueConnectionFactory</attribute>
<attribute name="RemoteJndiName">ConnectionFactory</attribute>
<attribute name="LocalJndiName">java:/JmsXA</attribute>
<depends>jboss:service=Naming</depends>
</mbean>
<mbean code="org.jboss.naming.LinkRefPairService"
name="jboss.jms:alias=TopicConnectionFactory">
<attribute name="JndiName">TopicConnectionFactory</attribute>
<attribute name="RemoteJndiName">ConnectionFactory</attribute>
<attribute name="LocalJndiName">java:/JmsXA</attribute>
<depends>jboss:service=Naming</depends>
</mbean>
</server>Services (startup)
Step 6 – ROB-EX 5.2 and later
The truststore location and password should be added to the service64\installSchedulerServerService.bat . Note this should be there already by default, so just verify the lines in highlightet are like shown below.
rem --- Scheduler parameters
rem Uncomment the following line when running with Turkish locales tr_TR !
rem set VM_OPTS=%VM_OPTS%;-Duser.language=en -Duser.country=US
rem add ssl truststore and password to vm options
set VM_OPTS=%VM_OPTS%;-Djavax.net.ssl.trustStore=conf/.truststore;-Djavax.net.ssl.trustStorePassword=XXXXXXXXX;-Dhttps.protocols=TLSv1,TLSv1.1,TLSv1.2Note, the password has been left out of this manual on purpose due to security reasons. Lookup the actual password for trustStorePassword from the file ganttServer\server\gantt\service64\installSchedulerServerService.bat
The service should be reinstalled in order for the changes to become active. To reinstall the service first remove it by running installSchedulerServerService.bat with argument uninstall. Then to re-install run installSchedulerServerService.bat without any arguments.
Step 7 – ROB-EX 5.0 and older
Server installs created prior to ROB-EX 5.2 uses the 32-bit service option configured in the file service\multiuserservice.conf. Make sure the lines in yellow below are added to the file. Important: in case a line already exists called wrapper.java.additional.2 – then add highlighted line below as wrapper.java.additional.3 instead.
# Java Additional Parameters
wrapper.java.additional.1=-Dprogram.name=../../../bin/run.bat
# SSL configuration
wrapper.java.additional.2=-Djavax.net.ssl.trustStore=conf/.truststore -Djavax.net.ssl.trustStorePassword=XXXXXXXXXXX -Dhttps.protocols=TLSv1,TLSv1.1,TLSv1.2Note, the password has been left out of this manual on purpose due to security reasons. Lookup the actual password for trustStorePassword from the file ganttServer\server\gantt\service64\installSchedulerServerService.bat
Finally in case the server is running in a console window started by a bat file (not a likely scenario for production), then add also the truststore location and password to the JAVA_OPTS in ganttServer/bin/run.bat
-Djavax.net.ssl.trustStore=conf/.truststore -Djavax.net.ssl.trustStorePassword=XXXXXXXXXXXX -Dhttps.protocols=TLSv1,TLSv1.1,TLSv1.2Note, the password has been left out of this manual on purpose due to security reasons. Lookup the actual password for trustStorePassword from the file ganttServer\server\gantt\service64\installSchedulerServerService.bat
Web based communication (Web Admin pages)
Step 8
Note this step is only necessary if you require a secure https connection for the web-admin pages. If you are just looking to secure the communication between server and clients, this step is not required.
To enable SSL in the Multiuser Web Admin pages, changes should be made to the file ganttServer\server\gantt\deploy\jbossweb-tomcat50.sar\server.xml. First add XML comments around this area of the file
<!--
<Connector port="8080" address="${jboss.bind.address}"
maxThreads="150" minSpareThreads="25" maxSpareThreads="75"
enableLookups="false" redirectPort="8443" acceptCount="100"
connectionTimeout="20000" disableUploadTimeout="true"/>
-->Then replace with this SSL/TLS Connector configuration part (i.e. paste text provided below just below the sections commented out above)
<!-- SSL/TLS Connector configuration using the admin devl guide keystore
-->
<Connector port="8080" address="${jboss.bind.address}"
maxThreads="100" minSpareThreads="5" maxSpareThreads="15"
scheme="https" secure="true" clientAuth="false"
keystoreFile="${jboss.server.home.dir}/conf/.keystore"
keystorePass="XXXXXXXXXXXX" sslProtocols=TLSv1,TLSv1.1,TLSv1.2 SSLEnabled="true" />Note, the password has been left out of this manual on purpose due to security reasons. Lookup the actual password from the file ganttServer\server\gantt\ssl\conf\ssl-domain-service.xml
At this point start the ROB-EX Server service again (Run->Services.msc)
The Web Admin can be accessed on the https://${jboss.bind.address}:8080/gantt/ or https://localhost:8080/gantt/
ROB-EX Client
The client setup properties for SSL must be changed by adding/modifying the lines below to the <client_dir>\custom\GanttSetup.properties file (typically add these lines at the top of the file):
-Djavax.net.ssl.keyStore=./config/ssl/.keystore
-Djavax.net.ssl.keyStorePassword=
-Djavax.net.ssl.trustStore=./config/ssl/.truststore
-Djavax.net.ssl.trustStorePassword=
-Dhttps.protocols=TLSv1,TLSv1.1,TLSv1.2Note that when using the internal ROB-EX generated certificate, passwords can be left as blank. Passwords needs only be specified when you want to use your own generated certificate.
Shop Floor
To enable HTTPS in Shop Floor changes should be made to the <client_dir>\plugins\shopfloor\site\conf\server.xml file. If Shop Floor is available as a public service on the internet, then it is strongly recommended to secure the communication with SSL.
The normal http connector should be comment out, like this:
<!--
<Connector className="org.apache.catalina.connector.http.HttpConnector"
port="80" minProcessors="5" maxProcessors="75"
enableLookups="true" redirectPort="18443"
acceptCount="10" debug="0" connectionTimeout="60000"/>
-->Then paste this SSL part just below the out-commented section.
<Connector className="org.apache.catalina.connector.http.HttpConnector"
port="443" minProcessors="5" maxProcessors="75"
enableLookups="true"
acceptCount="10" debug="0" scheme="https" secure="true"/>
<Factory className=
"org.apache.catalina.net.SSLServerSocketFactory"
clientAuth="false"
keystoreFile="../../../config/ssl/.keystore"
keystorePass="XXXXXXXXXXXX"
protocol="TLS"
keyAlias="gantt"
/>Note, the password has been left out of this manual on purpose due to security reasons. Lookup the actual password from the file ganttServer\server\gantt\ssl\conf\ssl-domain-service.xml
The default https port is 443 and Shopfloor can be accessed on https://localhost (i.e. notice it is not necessary to specify the port number, as 443 is the default port for https communication). If another port is preferred the port attribute should be changed.
In addition the client must be configured with SSL settings as described above in ROB-EX Client configuration.
REST Server Service
To enable SSL for the REST Server Service integration (used as example for communication with .NET based clients) add the https scheme usage as a parameter on the short cut for starting ROB-EX, or alternatively insert this line in custom/GanttSetup.properties:
-Dgantt.rest.scheme=httpsIn addition the client must be configured with SSL settings as described above in ROB-EX Client configuration.
Installing your own certificate
This section describes what tools to use in case you would like to install and use your own certificate, e.g. a certificate obtained from a trusted certificate authority (CA). The certificate provided out of the box with ROB-EX, is a self signed certificate. This certificate type has the following pros and cons:
- (+) it is free to use
- (+) it never expires (a certificate issues by a CA, will typically expire after 2 years)
- (+) it is secure, in the sense that transmitted data is encrypted in a robust and secure fashion
- (-) a browser will warn that the certificate is not issued by a trusted certificate authority. If you want to avoid the warning, the different browsers all have options a user can accept a self signed certificate as being safe (search the Internet for a how-to on the subject).
If you would like to install your own certificate, the certificate should either be generated or added to the keystore for the ROB-EX server and client sides. A tool that is part of the JDK from Oracle, called keytool and is located in the bin folder, is used for working with certificate stores
To generate your own certificate.
keytool -genkey -alias gantt -keyalg RSA -validity 36500 -keystore .keystoreIf you wish to add an existing signed primary certificate use this:
keytool -import -trustcacerts -alias gantt -file mycertificate.crt -keystore .keystoreThe client side need to use a truststore with the certificate. To do this, export from the keystore with the keytool:
Export the certificate from the keystore
keytool -export -alias gantt -keystore .keystore -rfc -file provider.cerImport the certificate into the truststore
keytool -import -alias gantt -file provider.cer -keystore .truststoreNew keystore and truststore files should be placed into
ganttServer\server\gantt\conffolder (server side)<client_dir>\config\sslfolder (client side)
SSL V3.0 “Poodle” Vulnerability
In order to address the SSL V3.0 “Poodle” Vulnerability the SSL3 protocol has to be disabled. This is done by direct specifying the valid TLS protocols as “TLSv1,TLSv1.1,TLSv1.2” which blocks for fallback to SSL3 when as described in this link: .
Further links that explains the configuration can be found at

Post your comment on this topic.